Recognize the Person, not the Credential.
Mimoto’s patent-pending technology dynamically analyzes human, environmental, and contextual factors to continuously recognize real-world individuals.
The Unique Power of Mimoto
AI-Powered Mimoto adapts dynamically to the available data streams, then applies multiple algorithms to determine with certainty who a specific person is.
It continuously recognizes and automatically responds in real-time to:
- Corporate account takeover / ransomware attacks
- Insider threats
- Who is using admin or root access
- Unauthorized access of customer data and other sensitive information

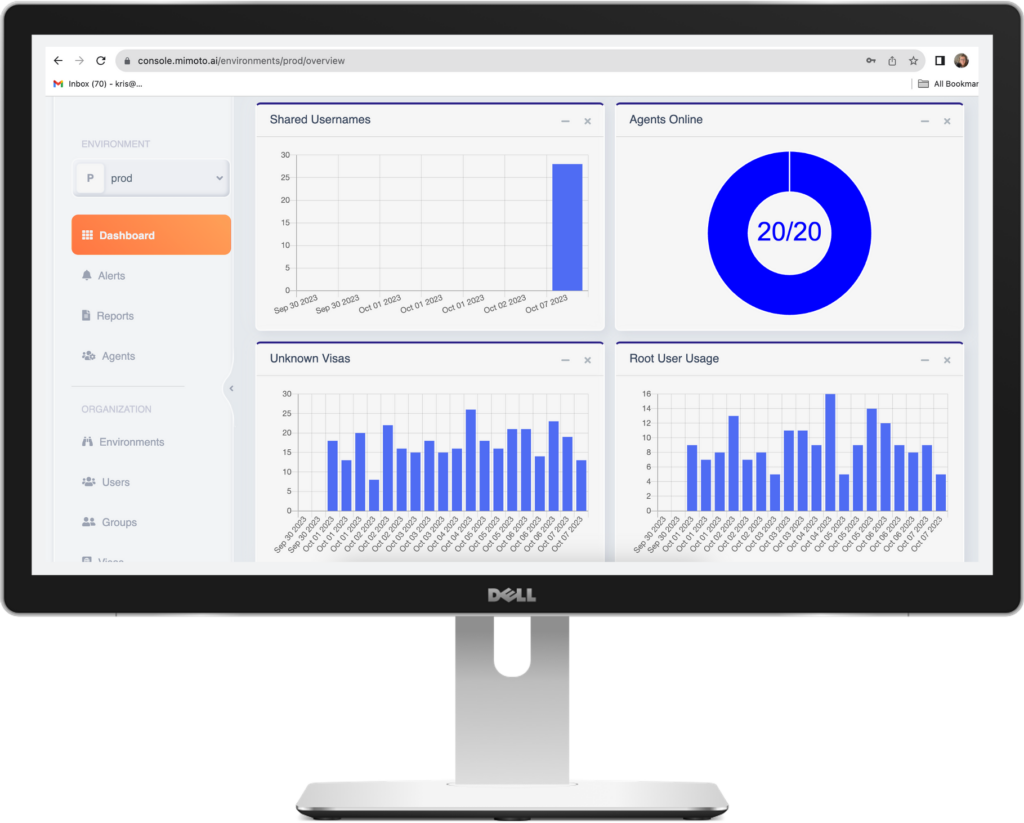
Continuous Real-time Person-specific Recognition for Account Take Over Detection, Access Enforcement, and Policy Compliance
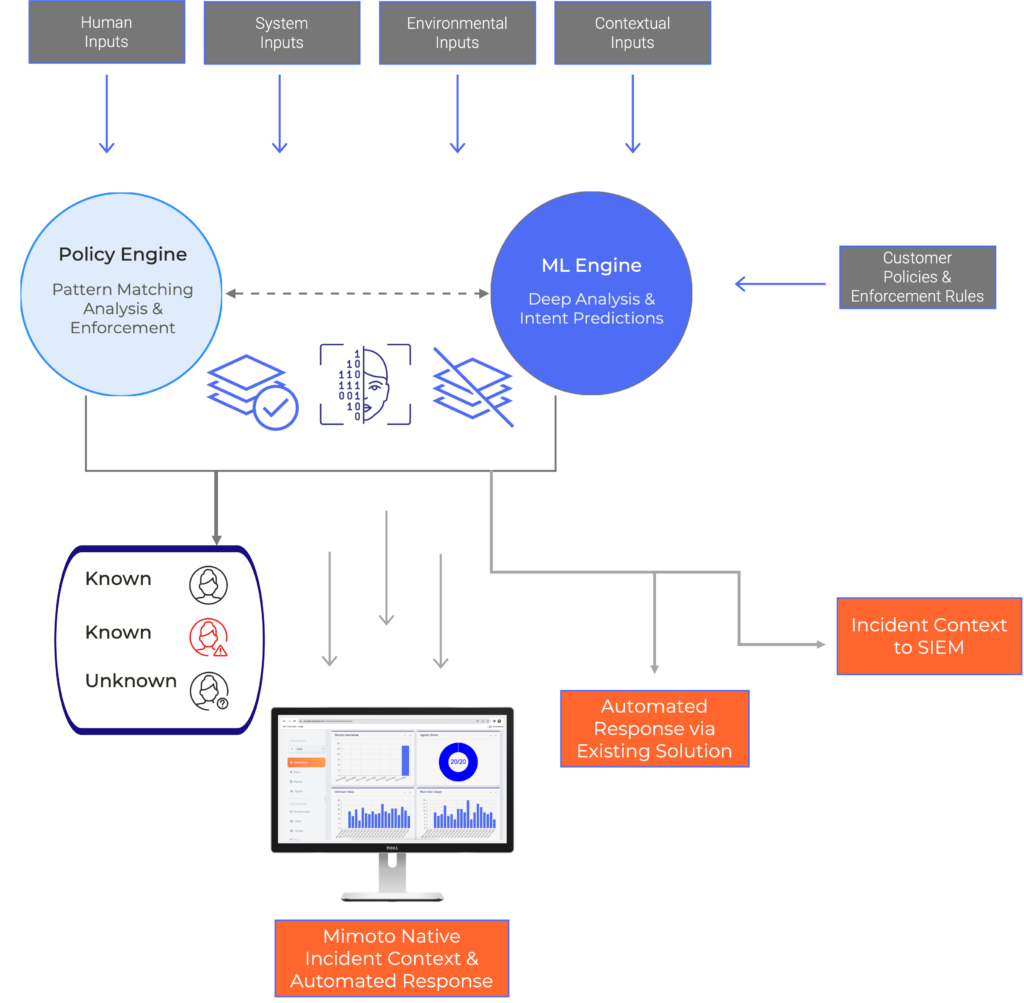
The Mimoto Platform recognizes which specific person is accessing systems, data, and apps, no matter how they are accessed. The platform’s dual ML/AL engine creates and pattern matches granular person-specific profiles for a 360-degree understanding of each person and the context of issues.

The Mimoto Integration Hub enables the delivery of real-time context and automated responses to account take overs (active ransomware attacks), protocol deviations or other nefarious activity.