
user_name ≠ Person
Mimoto’s AI-powered, person-based continuous validation knows with certainty when a user is being impersonated within systems and responds in real-time, BEFORE an attack is weaponized.
Person-based, Not Credential-based, Enables Real-time Response to…
Ransomware / Data Theft
Breaches BEFORE ransomware is launched OR your customers’ personal information is stolen
Covert Backdoor Software Access
Bad actors sneaking in through software or open source dependencies or backdoors injected into code
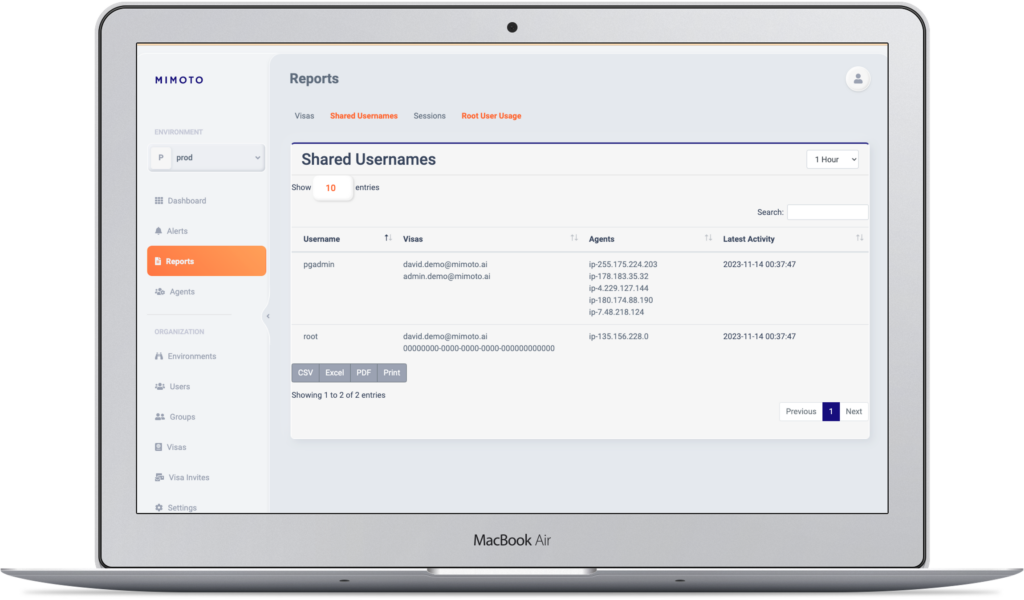
Privilege Access Exploitation
Who is using admin or root access or generic accounts
Remote Worker / Offshore Developer Impersonation
Know with certainty usage remote worker and offshore developer access is who it is supposed to be


