Despite billions in annual spending, identity-based attacks continue to dominate the threat landscape. Credential abuse accounted for 22% of all data breaches in 2025, 60% of breaches still involved the human element, and AI-enhanced attacks, from deepfake impersonation to industrial-scale brute force, are accelerating the crisis. The reason is deceptively simple: none of these technologies verify the person behind the session. They authenticate credentials, not people. The entire legacy digital security stack is built on a foundational assumption: that the entity presenting a credential is the person to whom that credential was issued. AI has transformed this identity gap vulnerability into a crisis.
Mimoto Continuous Verification Shifts the Paradigm!
Rather than monitoring what credentials are doing or flagging statistical anomalies in behavior, Mimoto continuously verifies who is performing each action. The platform builds AI-generated identity profiles that are unique to each individual and uses real-time pattern matching to confirm the person behind every session, every interaction, and every access request.
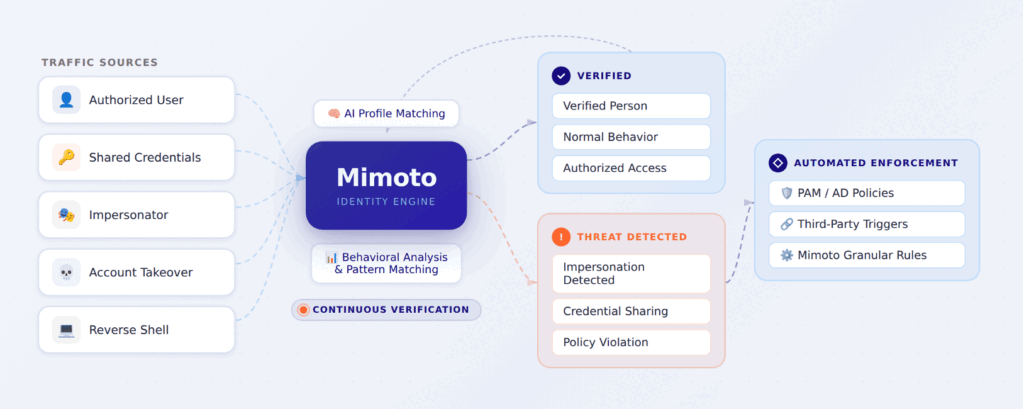
AI-powered MCV recognizes and responds in real-time when:
- a user is being impersonated by a person or agent
- an account is taken over
- a credential is shared or compromised
Straightforward & Simple Pricing
One profile per person, no matter how many places it is deployed. Mimoto can be deployed anywhere you want to protect.
Schedule a Demo & Trial
Experience Mimoto Continuous Verification first hand.
